How To Use Nmap:- Second and most important step of ethical hacking and penetration testing is port scanning. That’s where we use NMap and its handy features. In this tutorial, we will learn how to use nmap for port scanning.
NMap (stands for network mapper) is network scanning and host discovery tool. It is open source and created by Gordon Lyon. Nmap is mostly used for port scanning and discovering services on the target system by sending and analyzing packets.
The reason why nmap is best because it provides us with lots of features other than port scannings like host discovery, vulnerability scanning, operating system fingerprinting and discovering the services running on the target system and version of the softwares.
It is available in both command line and graphical user interface. Nmap is another favorite tool of hackers and cybersecurity experts.
Download and Install Nmap
In Kali Linux, nmap is already installed. You can access it by typing nmap in the terminal.
How To Use Nmap
We will learn to use nmap with its scanning types. So, let’s get started.
How To See Passwords in Chrome
Host Discovery
So, first, let’s do host discovery to see if the target system is up or not, or can we connect to the target or not? Most of the times, when you will use simple ping command tool to test whether your target is alive or not, it will tell you that target system is not alive or packet sent lost 100%.
Ping tool sends ICMP packets to test if the target system is up or not. But most of the times you will find that your targeted system has a firewall enabled, so you can not send ICMP packets by ping.
I have a windows machine which has a firewall enabled connected to my Kali Linux machine, and now I want to see if it is up or not. So let’s see if we can perform host discovery using ping or not.
Free Movie Streaming Sites No Sign Up Required
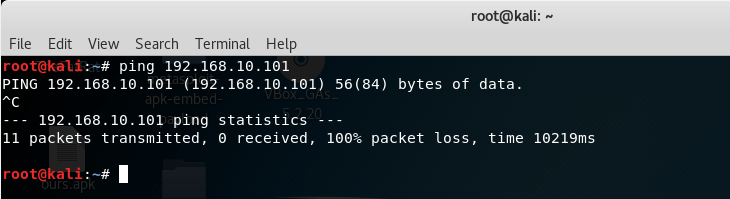
As you can see, it says that 11 packets transmitted but 0 packets received. It means our target host is not alive but it could also mean that the target system has the firewall enabled.
Now let’s use the arp-scan tool, this tool sends arp packets to the target system to see if the target is up for connection or not.
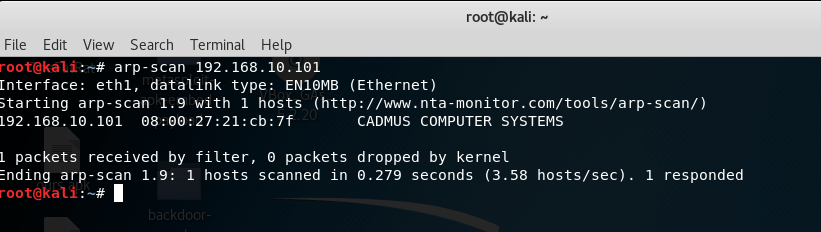
So, the arp-scan tool sent 1 packet and received 1 packet, it means that the target system up but has a firewall enabled.
I recommend you to first use ping tool for host discovery and if it doesn’t work then use arp-scan tool for same.
After the process of host discovery, our next step is to use nmap tool for port scanning. There are different types of port states recognized by the nmap tool. Let’s see what are these states and what they mean.
How To Hack Facebook Account Using Phishing Attack
Nmap Port States
We have six main states of ports when nmap scans for open or closed ports on the target system. We need to know the meaning of all these states before moving to the actual port scanning process.
Don’t worry it won’t take much time. I will explain in short and simple meaning.
Open
It means that the port is open, an application is running on that port and target system and application running on that port is actively accepting all the TCP and UDP connections.
Closed
It means that the port is open but there is no application on the target system running is on that port and target system is responding to the nmap probe packets on that port.
Filtered
It means that namp is failed to determine if port is open because some firewall, IDS or router is preventing the system from replying to nmap probe packets.
How To Hack Android Phone Using Kali Linux
Unfiltered
It means that the port is reachable but nmap failed to determine if it is open or closed.
Open|filtered
It means that nmap can’t determine if port is open or filtered because the open port is not responding.
Closed|filtered
It means nmap failed to identify if port is closed or filtered.
Learn How To Setup Ethical Hacking LAB
NMap Port Scanning Basics
Let’s see basic uses of nmap for scanning.
So, if you want to simply scan any target you need to use command nmap target_ip. For Example:-
nmap 192.168.56.1
If you want to scan an entire subnet, you will use nmap target_ip/24. For example:-
nmap 192.168.56.1/24
If you want to scan range of IP address, you can use nmap target_ip-range command. For example, if you want to scan IP addresses from 192.168.56.1 to 192.168.56.10, then the command will be.
nmap 192.168.56.1-10
For scanning a list of targets from a text file, use below command.
nmap –iL target_list.txt
To scan for specific ports on target system, use below command. For example, if you want to scan the target system for port 21 and 443, use this command.
nmap –p21,443 192.168.56.1
List of Best WhatsApp Tips Tricks and Hacks
NMap Port Scanning Types
These are the main types of scans in nmap.
OS Detection
We can use nmap to know which operating system is our target system is using. To do this we will use –O in below command. For example, I am running nmap scan with –O on my target system and let see the result.
nmap –O 192.168.56.1
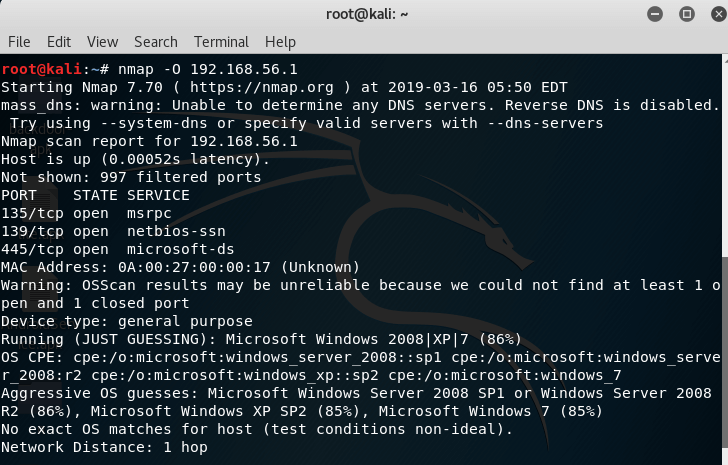
As you can see, it says that the target system is using Microsoft Windows operating system.
Learn To Hack Windows 7/8/10 Using An Excel File
TCP SYN Scan
It is also called TCP stealth scan, it scans for TCP ports in the target system and it doesn’t leave any trace or log of it, because it sends a syn packet and does not reply to ack. So it doesn’t make a full connection with the target system. Hence, no trace or log will be recorded.
To perform a simple syn scan, use nmap –sS target_ip.
nmap –sS –O 192.168.56.1
Here –s is used to declare the type of scan and –sS means SYN Scan or Stealth Scan. I also use –O command with it for OS detection.
TCP Scan
This type of port scanning in nmap is used to scan for TCP ports in the target system. Unlike SYN scan, it completes three-way handshake with the target system and makes the full connection. To scan for TCP ports in the targeted system, use nmap –sT target_ip. For example:-
nmap –sT –O 192.168.56.1
-sT is used to declare that we want to scan for tcp ports only.
How To Make A Virus Using Notepad
UDP Scan
As you can guess from its name, this is used to scan for UDP ports only, on the target system. To scan for only UDP ports, use nmap –sU target_ip. For example:-
nmap –sU 192.168.56.1
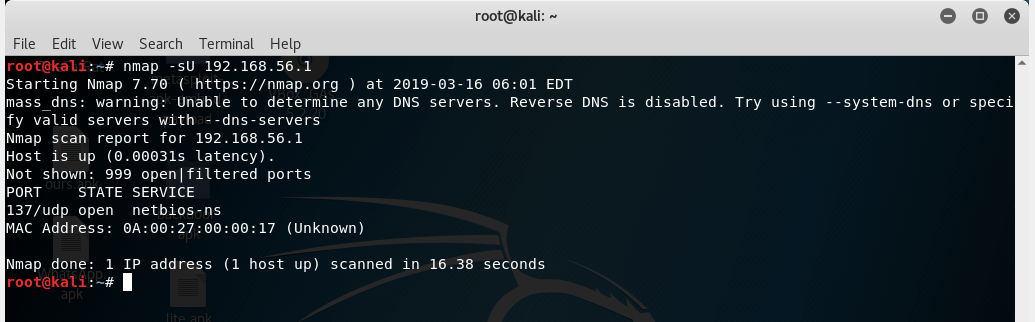
-sU is used to scan for UDP port scan only.
Introduction to Database Schema
FIN Scan
Most of the times, IDS or firewalls will prevent you to use SYN scan or TCP scan, because it won’t allow you to establish a connection. In this case, we can use FIN Scan. It will send the packets with FIN flag. To perform FIN scan, use nmap -sF target_ip. For example:-
nmap –sF 192.168.56.1
PING Scan
Ping scan is not basically a scan type for port scanning in nmap. It’s unlike other scan types, used to see if the target system is alive or reachable or not by sending ICMP packets. It requires root privileges. To perform ping scan, use nmap –sP target_ip. For example:-
nmap –sP 192.168.56.1
How To Hack Android Using Spynote RAT
Idle Scan
Idle scan is a really interesting one. This scan in nmap provides you with furthermore level of anonymity. Idle scan doesn’t send packets from attacker’s IP address to target IP address, instead, it sends packets from one host on the network to target system. We call that host zombie system.
To perform this scan, use nmap –sI zombie_system_ip target _ip. Where zombie_system_ip is IP address of any system on the network that nmap will use to communicate with the targeted system and target_ip is IP address of our targeted system. For example:-
nmap –sI 192.168.56.6 192.168.56.1
In the above command, nmap will send packets from 192.168.56.6 (which is on the same network as target system is) to 192.168.56.1
Learn To Port Forward Without Router
Version Detection
So now we know about the open ports on the targeted system. But after that, now, we need to the version of application and name of the app running on the port in the target system. That’s where we are gonna use version detection.
To perform version detection, use nmap –sV target_ip. For example:-
nmap –sV 192.168.56.1
Now, have a look at the results.
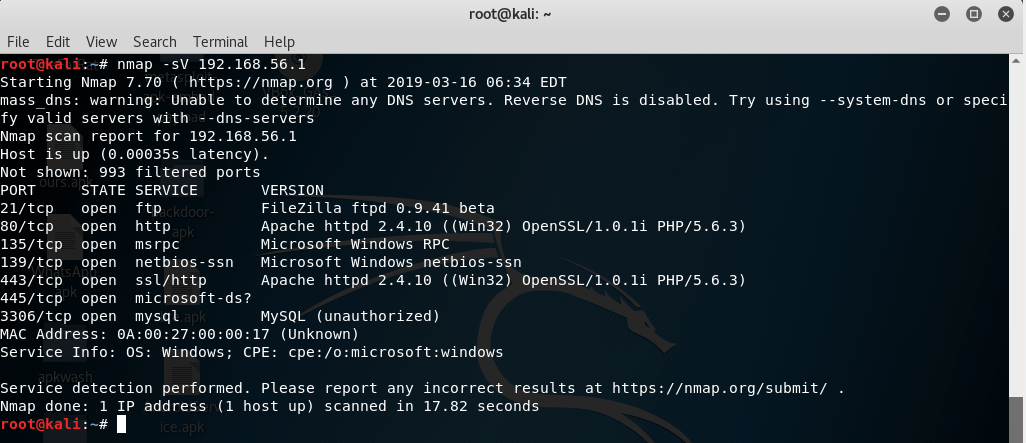
As you can see, when I performed version detection using nmap, it gives the name and version of apps running on ports.
Download Best Wi-Fi Hacking Apps For Android
Conclusion
In this post, we saw how to use nmap, nmap port scanning types and more. In our next post, we will learn to use nmap scripting engine.
To get the latest updates, please like our facebook page or subscribe to our newsletter using the email subscription form.
And please please share this with your friends and support us.